Source Link Privacy.
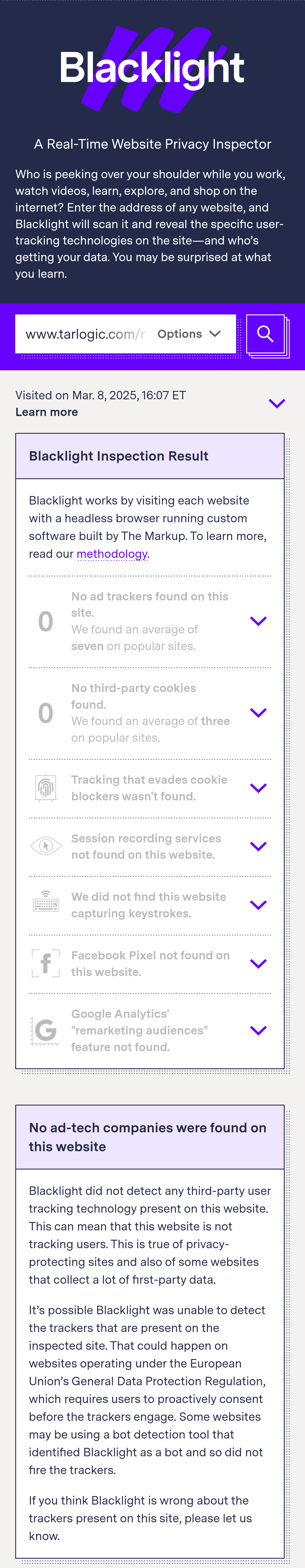
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


The article is a security company
trying to hype their companyruining their reputation in an incredibly ill-thought out attack that companies will ABSOLUTELY remember.Even worse, it just makes this security company look incompetent. Like a home security company that announces a huge vulnerability in Schlage locks- there’s a key that can unlock the lock included with every lock sold!!11!!!11!one!
I agree, but unfortunately, this has become common since Heartbleed, and they seem to be able to sell their snake oil to CTOs…