- cross-posted to:
- android@lemmy.world
I thought Google wallet generated a unique card id for every transaction.
This is a interesting bug, but I think fairly niche. Not many people use app pinning at all.
If the PoS supports tokens, it’ll use unique tokens for each payment. If the PoS doesn’t support tokens, the phone has a virtual credit card number linked to the real one, so if it does get stolen, you can just remove the card from your Google Wallet to deactivate it. Your real card number is never exposed.
Even then, credit card numbers on their own aren’t that useful anymore. Any online payment needs the CVC and PoS devices usually require chip or tap cards, which don’t use the number. On top of that, credit card companies have purchase price restrictions when using swipe because of the security risks vs chip (which is why most PoS devices don’t support swipe anymore).
Great explaination. Thank you
“which is why most PoS devices don’t support swipe anymore”
huh?
I didn’t even realize “app pinning” was a thing.
[This comment has been deleted by an automated system]
Turn off NFC unless you are using it at that moment.
Woah, first I learned of this. https://www.lifewire.com/turn-off-nfc-to-secure-your-android-smartphone-2532822
Kinda sucks that there’s no quick button for that. I can turn off Bluetooth, wireless, auto-rotate, etc in a single setting but not NFC?
I’m so envious of you. I don’t have that.
I don’t have NFC at all. Ultimate safety.
Sad
Which system do you have, with the NFC quick toggle?
Pixel 4a w. GrapheneOS, but I’m pretty sure I had that too on the stock ROM
Edit: OK, WTF. Apparently I misremember it or I actually had a version with that toggle. Some say it has been removed and some say it never was there in the first place.
I have a pixel 7 with android 13 and the NFC toggle is not on the quick buttons
Apparently they removed it or it never was there in the first place on AOSP
I can confirm it’s there on Galaxy S7 with Android 8
P7P with Android 13, I don’t have it. Wonder why it was removed…
I have it on Android 13 on my Motorola.
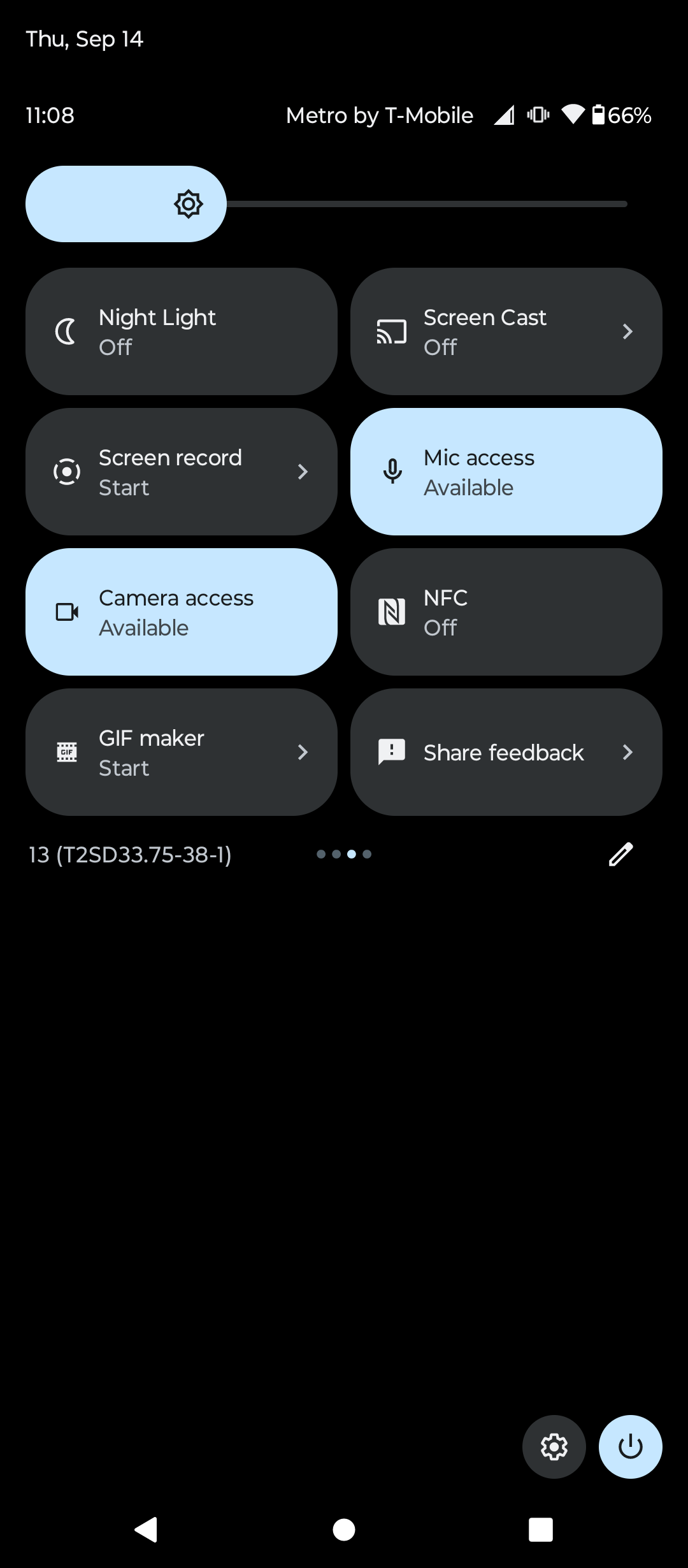
Many Samsung devices have a quick button for NFC toggling in their drop down menu, not sure about other phones though.
I have a Samsung Galaxy Watch, it has a button for that too. But also the Wallet app on the watch has to be manually opened to use it anyways, it’s not passive background app. I think I might just disable NFC on my phone and stick to using my watch for payments.
You can diasble all sensors and make a quick button for it in dev settings, dont remember how exactly it is called tho
You can try using Tasker to create a task that turns on NFC and launches Google Wallet / Pay afterwards.
After that, create another profile to turn off NFC when the screen is locked.
deleted by creator
great
The loophole seems to be having an app pinned to the screen (I’ve never done this, but it presumably keeps the phone from locking) while requiring you to have an unlocked phone to use NFC payments. This doesn’t seem to be a common scenario (I can imagine doing this in some sort of kiosk mode, or giving the phone to a kid and locking the app so he can’t wander around).
This is why Samsung pay is king, the NFC only turns on when you’re using Samsung pay otherwise it stays off









